Originally posted in Security Magazine November 27, 2019
There’s a great story on survivorship bias from World War II about a statistician named Abraham Wald. Bombers were getting hit by enemy fire on a regular basis, and losses of bombers were high. Researchers in the center for naval analyses were tasked with figuring out how to increase the survivability of the planes, and they initially recommended that armor be added to all the areas of the plane that showed the most damage when they returned to base. They reasoned that if these were the areas where planes were being hit the most, then armor there would stop the most hits:
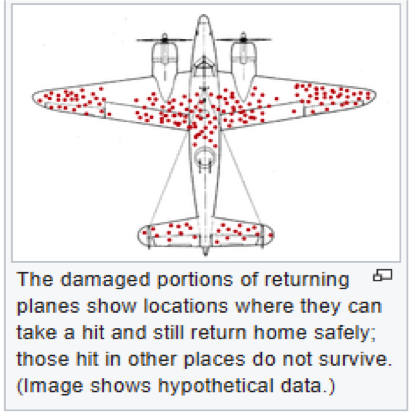
But when Wald looked at the study, he recommended something different – that armor instead to be added to the areas of the planes where no damage was detected. This is because the only planes that the team could study were those that made it back to base. Planes that didn’t make it back to base were probably being damaged differently – in ways that were not survivable – than those that did.
In cybersecurity, we can think about how to apply this same type of reasoning to breach data, like what we find in Verizon’s Data Breach Investigations Report (DBIR). In this study, when we look at successful breaches, (those that survive their encounters with a defender), we can see a pattern of defender action that is typical in a breach situation:
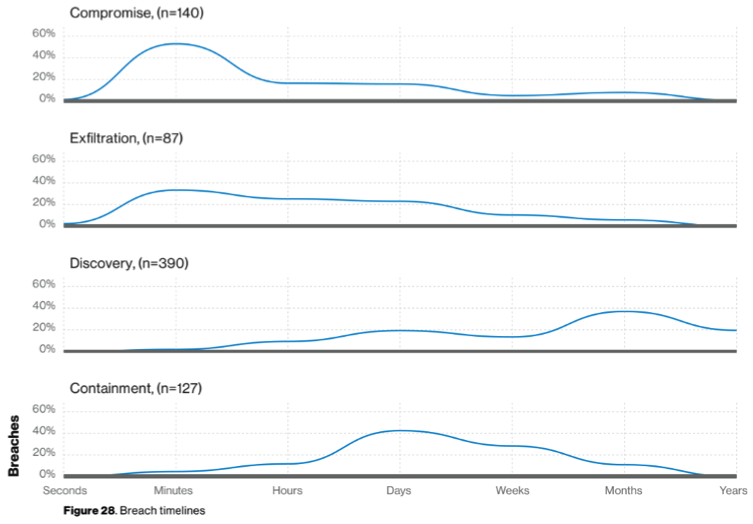
If we think about this from the perspective of a defender who wants to know what they can do differently to not suffer from a breach, the more interesting thing is what we don’t see. There are simply no reported breach situations where a defender discovered and started containment within seconds to minutes of the initial attack.
If the defenders manage to become aware soon enough and start containment, they generally win, or the attackers give up and move on. From the DBIR, we can see the magic line for discovery that kills attacks in progress is measured in seconds to minutes. If you can become aware of it that fast, chances are your defenders can stop the incident from becoming a breach.
That’s generally far easier said than done, however, and for many smaller companies, almost impossible. How can you afford to bring discovery time to seconds or minutes when that means staffing security experts to review all the signals coming in – even in the middle of the night – and those signals are almost never real incidents anyway?
This is one of the main reasons why mid-sized organizations are increasingly putting their hope in Managed Detection and Response (MDR) providers who focus on real-time triage and investigation into new signals as they happen. By having the staff on hand to support the pace of alerts from security devices coming in, and leaving them tuned up as sensitive as they can go, MDR providers work on the assumption that everything reported by those devices is a potential breach unless they have direct evidence to the contrary. Working from that approach means they can set much more aggressive targets on timelines for discovering and stopping potential attacks.
Organizations must take seriously the implication raised by the Verizon’s DBIR that containment needs to happen fast, too. To be successful, the cybersecurity industry needs to empower security analysts with the ability to contain an incident within seconds of detection.
And as the Verizon data shows, most incidents just don’t seem to survive long enough to turn into a serious breach when they encounter defenders who respond quickly and efficiently to each event, right after the initial compromise.








